Blog
The Secret Ingredient in the Alphabet Soup of Cybersecurity
This is the first in a series of blogs exploring how the Quine Streaming Graph analytics engine is the secret ingredient in the Alphabet Soup of cybersecurity, enabling faster, more accurate detection of complex threats without compromising on the type or volume of data analyzed, the fidelity of...
Streaming Graph Get Started
It's been said that graphs are everywhere. Graph-based data models provide a flexible and intuitive way to represent complex relationships and interconnectedness in data. They are particularly well-suited for scenarios where relationships and patterns are important, but until recently, they have...
Streaming Graph for Real-Time Risk Analysis at Data Connect in Columbus 2024
After more than 25 years in the data management and analysis industry, I had a brand new experience. I attended a technical conference. No, that wasn’t the new thing. At many conferences, I’ve been surrounded by data scientists, business analysts, data engineers, mathematicians, developers,...
Cypher all the things!
Uses for individual data engineering technologies are often broadened to more than just interacting with databases. The same goes for graph database techniques and, specifically, the leading language for building and querying graph databases – Cypher.
thatDot CEO Explains Streaming Graph to Cybersecurity Thought Leader
Briefing Room on demand webinar on thatDot Youtube channel: The Unreasonable Effectiveness of Streaming Graph thatDot founder and CEO Ryan Wright discussed the power of thatDot Streaming Graph and Novelty to detect the most well-hidden threats with the Bloor Group's Eric Kavenagh and Mark Lynd,...
Microservice Hell: The State of the Art in Streaming Services
Exploring the challenges of data processing in microservices, the article introduces thatDot’s Streaming Graph, which seamlessly integrates various data sources like Apache Kafka, AWS Kinesis, and more.
4 Advantages to Streaming Analytics in Graph Form
Explore the transformative benefits of streaming analytics in graph form, including real-time insights, deep relationship analysis, immediate categorical data processing, and drastically reduced mean time to value (MTTV).
The Future of Modern Threat Hunting is Streaming Graph
Standards-based threat detection & automated response using Quine streaming graph.
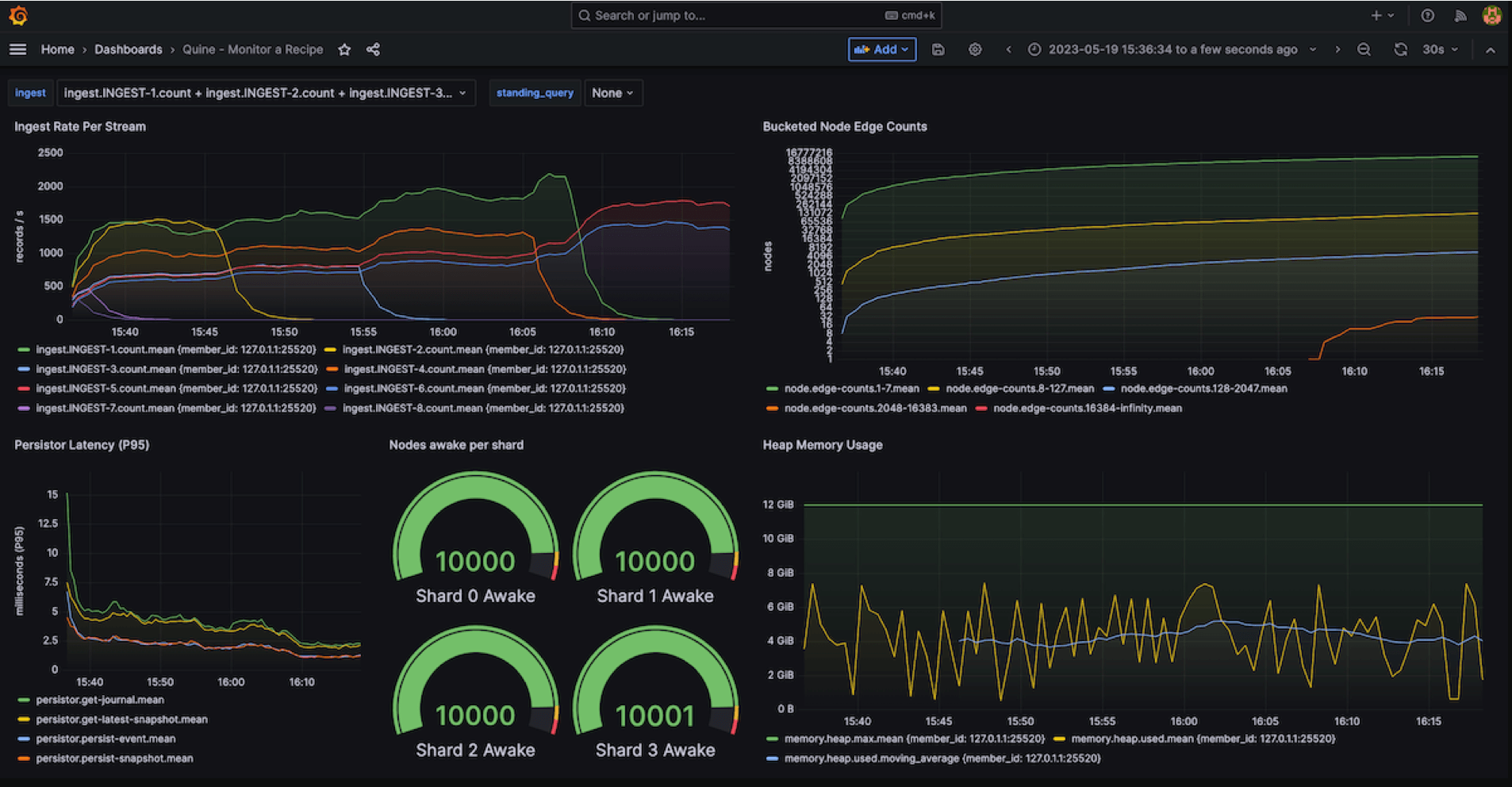
Monitoring Quine Streaming Graph using Grafana + InfluxDB
Monitoring tools like Grafana work well with Quine but there are a few things to keep in mind when monitoring data in motion.
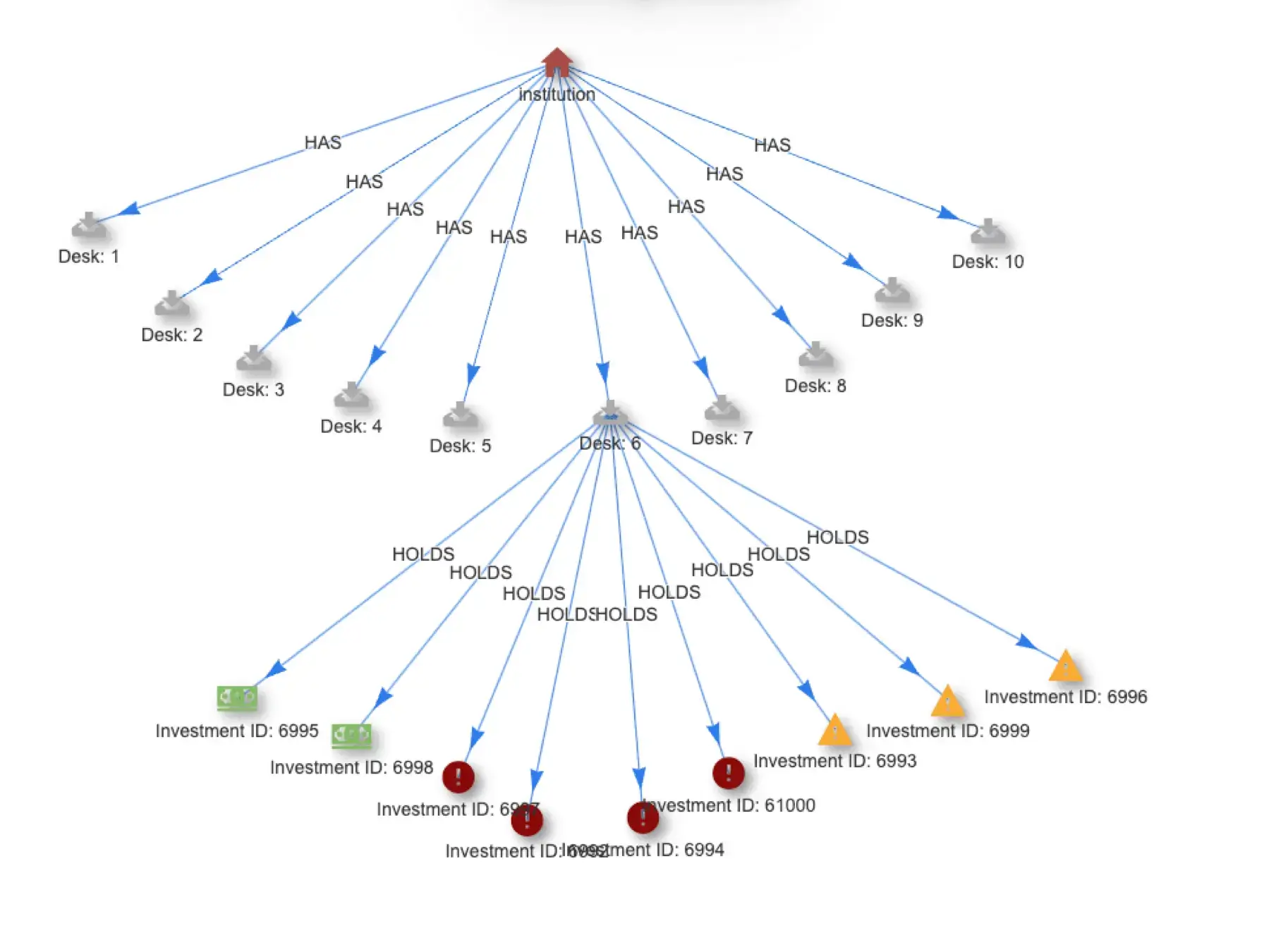
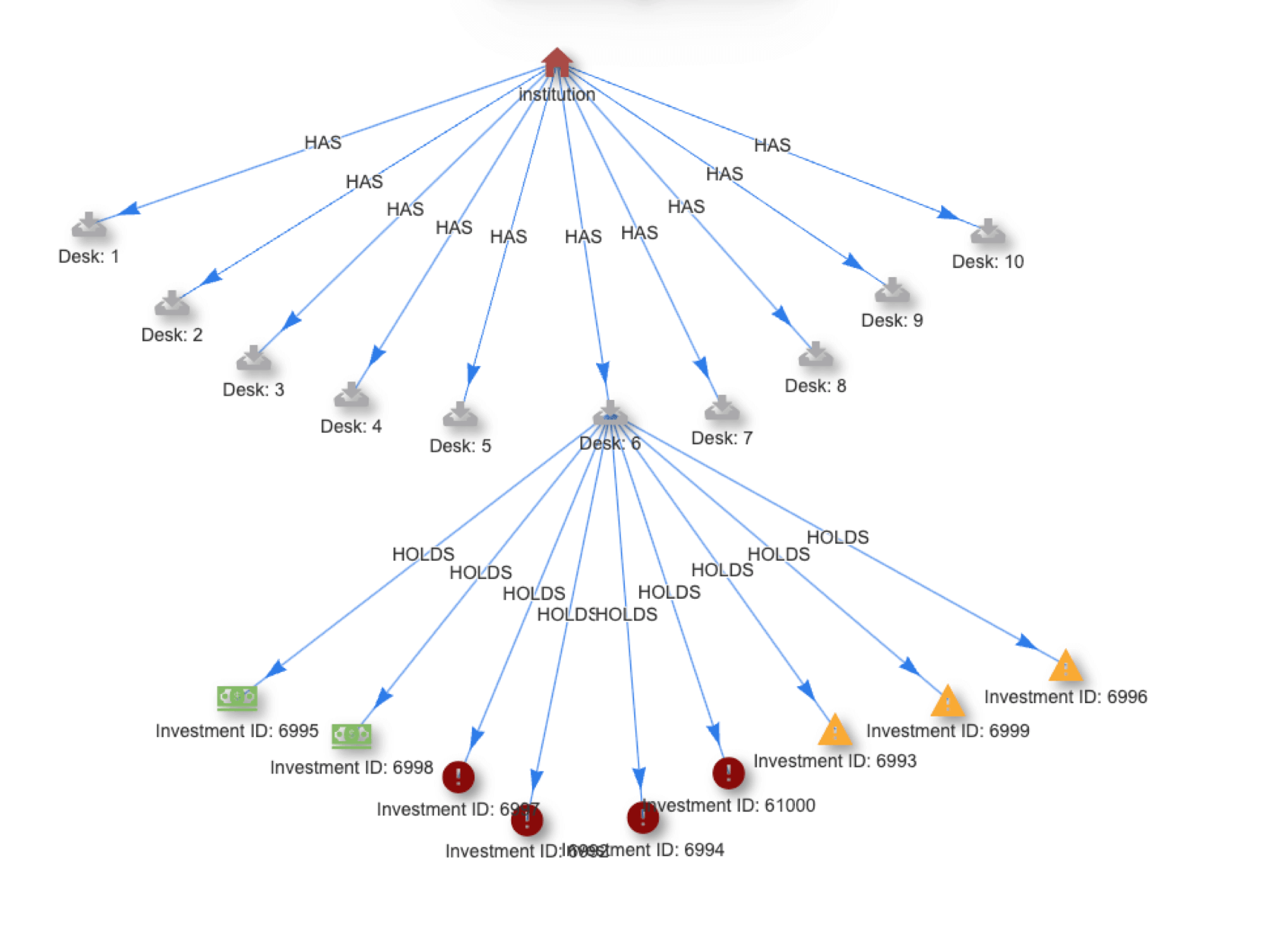
Calculate Risk and Optimize Asset Allocation in Real Time
Asset allocation and risk calculations need to move from batch to real time to free assets and improve compliance. Quine Streaming Graph provides a path.
Create a Quine Icon Library with Python
Add some flair to your Quine streaming graph visualizations while learning about the API at the same time.
Dynamic Duo: Quine & Novelty Detector for Insider Threats
In a big update to the VAST Advanced Persistent Threat blog, we demonstrate an end-to-end Quine plus Novelty Detector workflow.
idFrom(): the simple function that’s key to Quine streaming graph
idFrom() seems like a simple function for generating node IDs but it is the key to Quine’s ability to find complex patterns in high volume event streams.
Using Indicators of Behavior (IoB) Analysis for IoT data
Indicator of Behavior (IoB) analysis is extending beyond the cybersecurity domain to offer new value for finance, ecommerce, and especially IoT use cases.
Quine’s Real-time Temporal Event Sequencing Produces New Insights
Quine’s standing queries, idFrom + deterministic labelling can be use to efficiently create any subgraph you need (e.g. sequence based) in real time. This makes alerts more timely and root cause analysis more efficient.
Graph Neural Networks for Quine
Quine 1.5 includes support for graph neural network techniques like Node2Vec and GraphSAGE. This post provides an overview and tutorial.
Categorical Data: An Untapped Source of Real-Time Insights
Categorical data is an oft-ignored source of valuable business intelligence. Quine makes it easy to process categorical data with your existing ETL pipeline.
Why Digital Twins Need to Go Real Time
For digital twins to be truly useful in business operations, they must be able to drive actions and do so the instant an issue emerges, perhaps even beforehand.
What is the difference between batch and stream processing?
Stream processing offers the opportunity to detect important patterns in information and act in real time.
Scaling Quine Streaming Graph to Process 1 Million Events/Second
Learn how Quine achieves groundbreaking performance for real-time complex event processing and how you can reproduce the results.