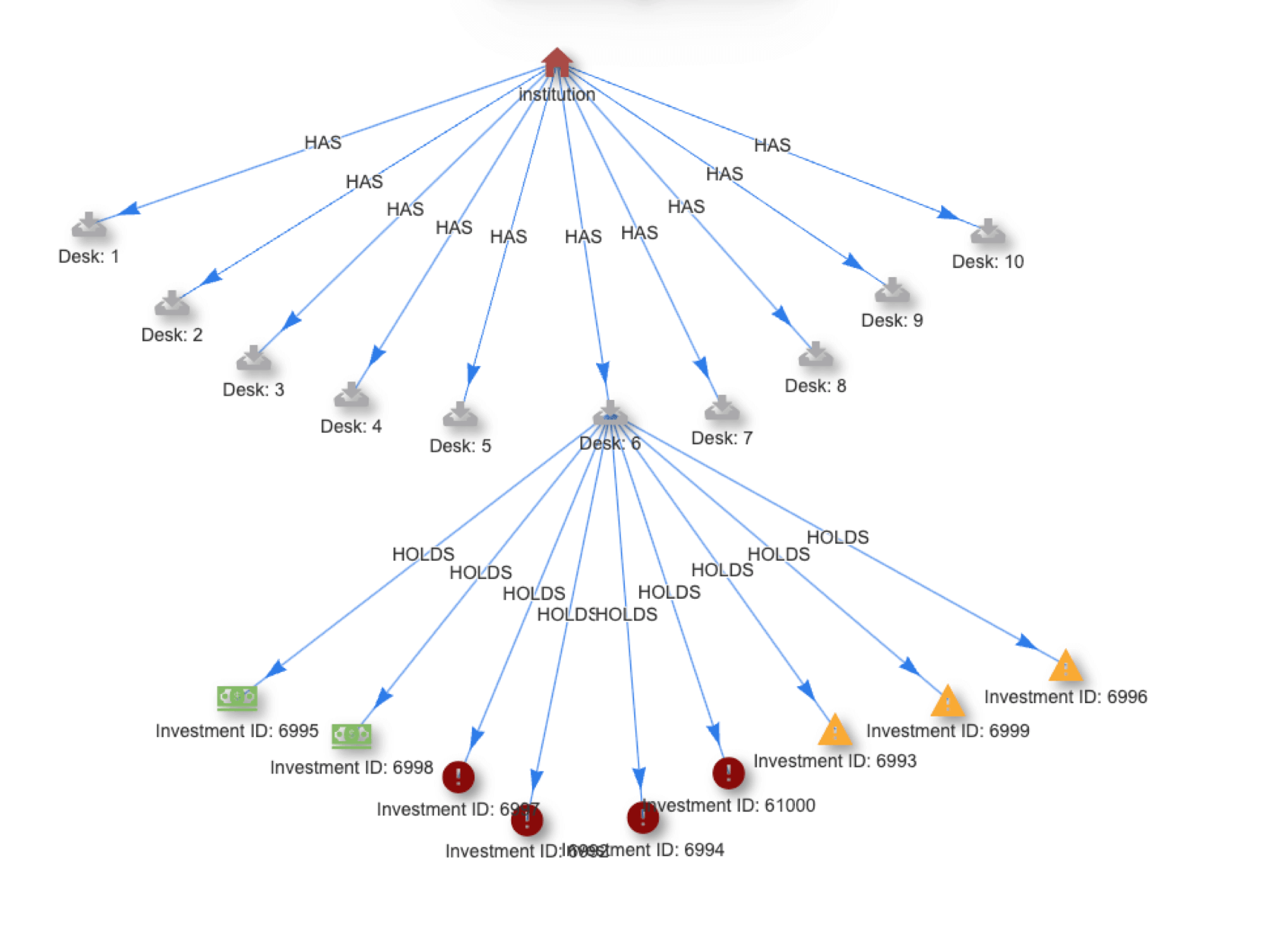
The Problem Metered attacks that generate low volume log-in attempts, from diverse IPs and across extended time frames, are designed to avoid the "3 strikes in 24 hours" business rules in authentication applications and the more complex analysis of log analytics / SIEM platforms. Batch solutions by definition cannot react until after a compromise has occurred while all real-time solutions impose time windows -- any data falling outside these rolling windows, no matter how important, is simply...
Authentication Fraud
read more